Users
The user refers to an individual who interacts with the application to accomplish tasks, access information, or utilize features provided by the application.
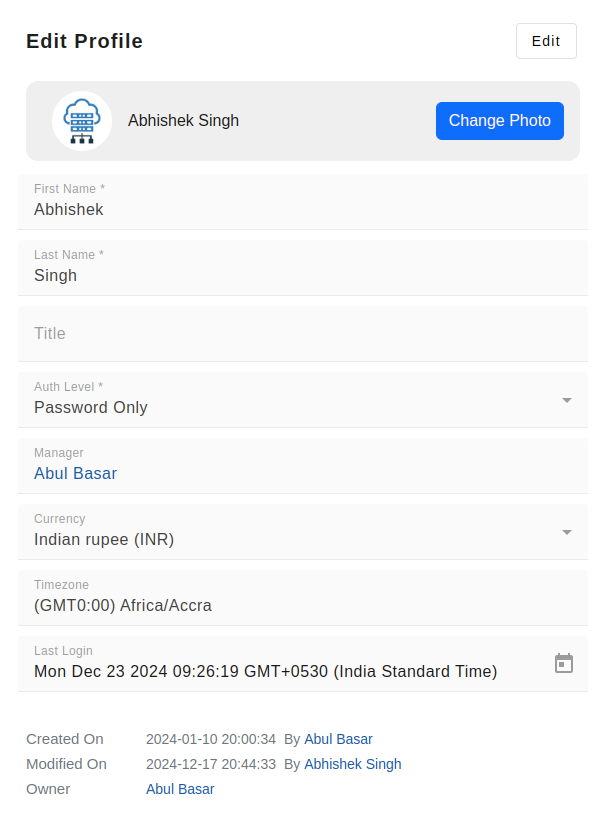
Basic user details
Basic details of a user typically include essential information about an individual
| Field | Description |
|---|---|
| First Name | User's given name. |
| Last Name | User's surname or family name. |
| User's email address, which serves as a unique identifier for login and communication. | |
| Title | User's job title or position within an organization. |
| Mobile | User's mobile phone number, which may be used for communication or verification purposes. |
| Status | User account status such as active, Locked, and Inactive. Status field controls authentication. Only active status allows the user to login or invoke API request. |
| Role | User's role controls the application features and data she can access. |
| Address | Official address for billing purpose. It includes fields - street, city, state, postal code, and country |
| Login Security | User's authentication level. User can opt for multi factor authentication for higher degree of login security. |
| Manager | User's manager or supervisor within the organization. |
| Timezone | User's local timezone. |
| Currency | User's Currency of choice. It is used for billing purpose. |
| Last Login | User's last login to the application. |
| Email Verified | It indicates whether the user's email address has been verified or confirmed, typically through a verification process involving an email confirmation link or code. |
User Role
User role plays a crucial control of the user's access to the application. There are two types of users - Administrator and Standard User. Following the principle of zero trust, Administrator has full access to the application, including features, functionalities and data, however, Standard User has no access to the functionality and data by default. Administrators need to provide explicit permissions to the Standard user so that they can access specific intended features and data.
Administrator: An administrator is an individual who is responsible for managing, configuring, and maintaining a system, network, application, or organization. tasks such as:
-
User Management: Administrators manage user accounts, including creating new accounts, modifying user permissions, resetting passwords, and deactivating or deleting accounts as needed.
-
System Configuration: Administrators configure and customize system settings, preferences, and options to meet the needs of users and the organization. This includes setting up network configurations, security policies, and other system parameters.
-
Security Management: Administrators are responsible for ensuring the security of the system or network by implementing security measures such as firewalls, antivirus software, encryption, access controls, and intrusion detection systems. They monitor for security threats, investigate security incidents, and take action to mitigate risks.
-
Data Management: Administrators oversee data management processes, including data backup, storage, and retrieval. They ensure data integrity, availability, and confidentiality by implementing backup strategies, data encryption, access controls, and data retention policies.
Standard User: A "standard user" refers to a user account with limited privileges and permissions. Standard users typically have access to basic functionality and resources within the system, but they are restricted from performing certain administrative tasks or accessing sensitive information.
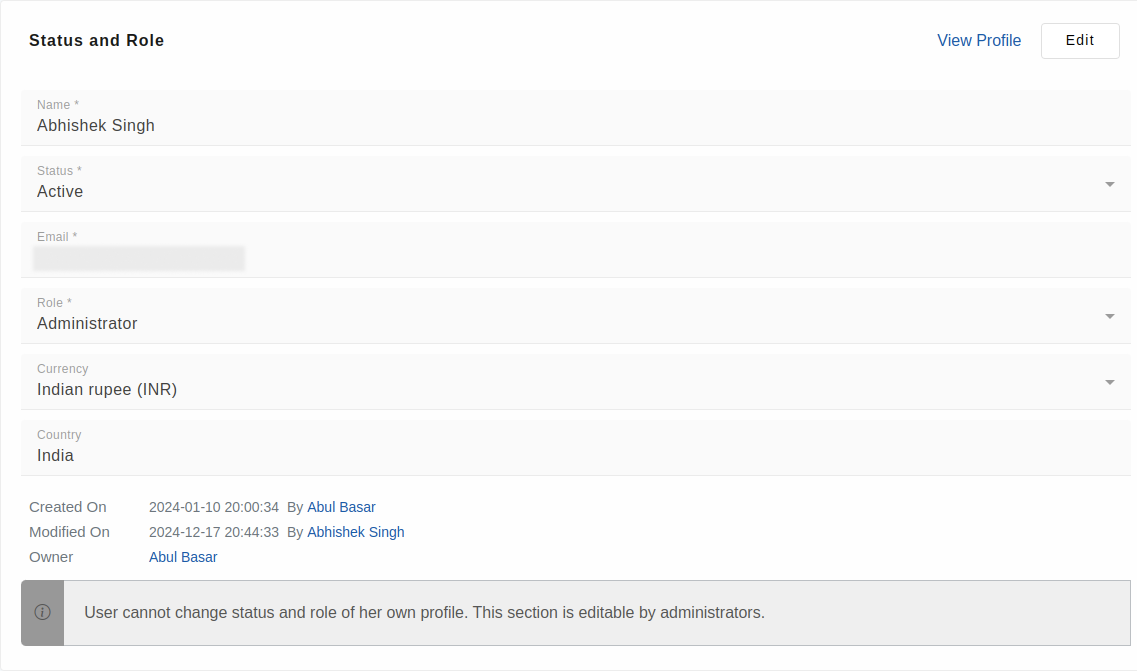
User Status
| Status | Description |
|---|---|
| Active | This status indicates that the user account is currently active and accessible. Users with an active status can log in, perform actions, and access resources in accordance with the authorization settings. Even for the API tokens to work, the corresponding account must be in active status. |
| Locked | If the user login attempts fails for a number of successive times, the account becomes locked. This status indicates that the user account has been temporarily locked. Administrator explicitly needs to set the status back to "Active" status to reactivate the user's account. |
| Inactive | This status indicates that the user account is currently inactive or disabled. Users with an inactive status may have voluntarily deactivated their account or may be temporarily suspended by an administrator. |
Status and role change
A user cannot status, role or any permission settings of her own profile. This restriction is applicable for the administrators as well. The administrators can change the role, status and other permission related settings of the other users from the administrative user details view. Any change to the status and role is notified to the user by email.
Login Security
Following are the login security features currently available in the application
-
Choose authentication mechanisms
- Password Authentication
- multi-factor authentication: Password authentication followed by email token verification for .
- Login using OAuth2 provider such as Google.
-
Login History: each login attempt is recorded which captures originating IP address, timestamp, and user-agent.
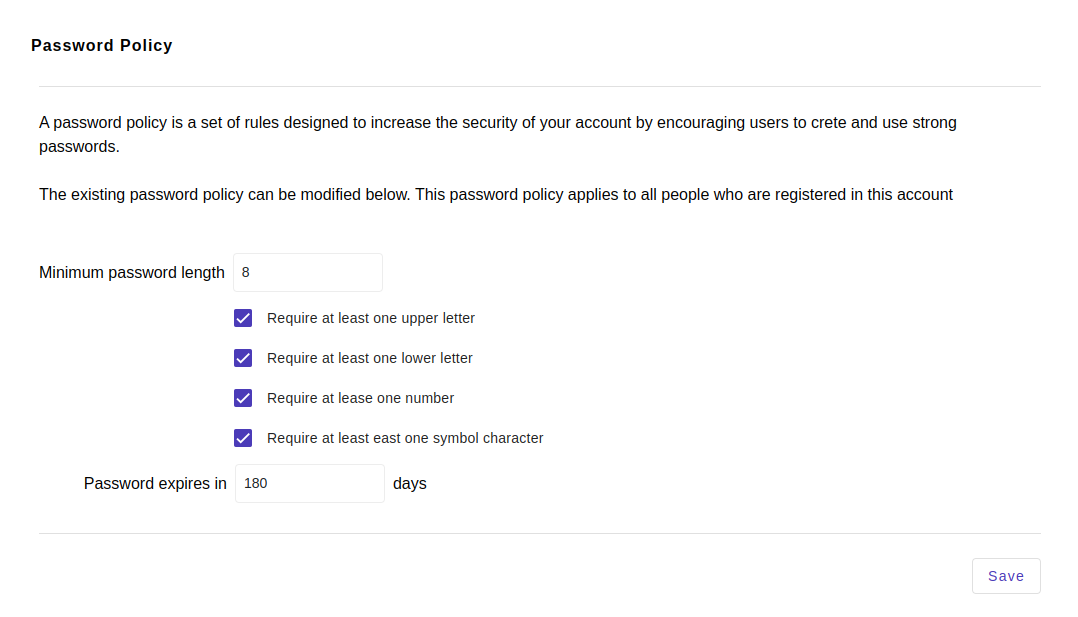
- Password Policy: Custom password policy for all users in the organization. The default password policy are below.
- Enforce password reset after administrator resets the password.
- User activity tracking: [On demand] record user activities including the API request details.
- Set session expiration duration. By default, each session expires in 24 hours. User and administrator can expire all sessions, thus inactivate all session tokens created for the user including the API tokens.
Default Password Policy
Email Verification
User needs to verify her email before performing normal operations in the application. Users who have select OAuth2 authentication provider are excepted from the email verification required.
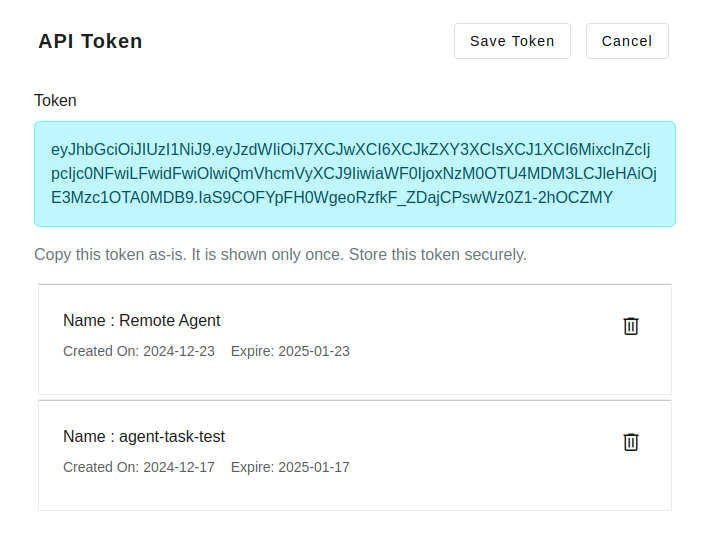
API Token
To use REST api, remote agent, or python SDK, you will need authorization token. Authorization token is a JSON Web Token(JWOT) which must be included in every request headers that are restricted to the authenticated users only. All users are allowed to create API token for her account. At a given time, only two API tokens can be created for a single user account. While creating a API token, you need to specify the expiry date - the date after which the token becomes automatically invalid.
You can delete an existing token, which deactivate the token. After the deleting the token, it may take up to five minutes (5 minutes) before cached session ids are also cleared.